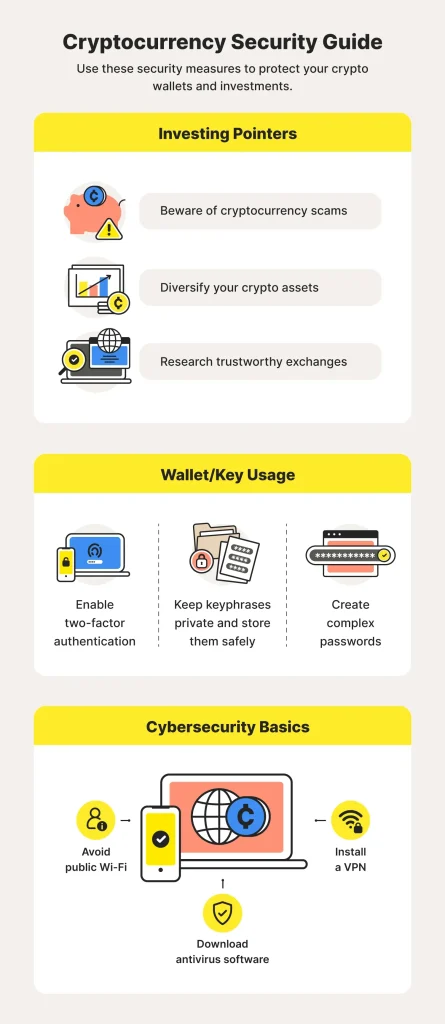
Cryptocurrency security best practices are essential for anyone protecting digital assets. As the crypto ecosystem expands, threats from phishing and malware persist, demanding disciplined habits and robust technical controls. A strong foundation combines crypto wallet safety, careful key management, and protective authentication measures to reduce risk. Adopting hardware wallets for long-term storage and using two-factor authentication on critical accounts further strengthens defenses. Finally, prioritize secure exchanges and maintain phishing protection while staying vigilant against social engineering.
In other words, protecting crypto holdings hinges on combining technical safeguards with disciplined routines. When discussing digital asset protection, think of secure storage, trusted exchanges, and robust authentication as a single, layered shield. Beyond wallets and seeds, ongoing awareness of phishing attempts, device hygiene, and routine reviews of active sessions keeps risk at bay. Adopt a governance mindset that includes regular firmware updates, multi-signature options where available, and diversified custody across reputable hardware devices and exchanges. Finally, practice periodic drills to verify backups, rehearse disaster recovery, and ensure family members understand basic security cues. In practice, maintain backups offline, verify seed integrity periodically, and store recovery data in tamper-evident formats. By integrating these measures into everyday routines, individuals can build a resilient security posture that scales with their holdings.
Cryptocurrency security best practices: layered defenses for digital asset protection
Cryptocurrency security best practices form a layered defense that combines technical controls, disciplined habits, and ongoing vigilance to protect digital assets. As threats evolve—from phishing attempts and malware to exchange breaches— a comprehensive strategy helps you minimize risk and preserve value. This approach foregrounds crypto wallet safety, strong authentication, and prudent platform choices as core pillars.
Practical steps include using hardware wallets for long-term storage, separating hot and cold storage, and protecting seed phrases with durable backups. For daily access, maintain a smaller, internet-connected balance while keeping the bulk of funds offline. Enhance crypto wallet safety with unique passwords managed by a reputable password manager, consider multisignature setups where supported, and consistently verify transactions on-device to avoid errors.
Enhancing crypto wallet safety and authentication: 2FA, hardware wallets, and secure exchanges
Effective authentication hygiene is a cornerstone of security. Implement two-factor authentication on all critical accounts using an authenticator app rather than SMS, and, where supported, use hardware security keys (FIDO U2F/WebAuthn) for stronger phishing resistance. These measures, together with ongoing phishing protection awareness, strengthen crypto wallet safety by reducing credential theft risk.
Choose secure exchanges with transparent security practices, enable withdrawal whitelists and multi-step confirmations for large transfers, and regularly review devices and sessions to revoke access from unused systems. Keep software up to date and prefer diversification of storage across multiple secure exchanges and wallets to avoid single points of failure.
Frequently Asked Questions
What are the essential crypto wallet safety practices to protect my funds?
Crypto wallet safety starts with securing private keys and seed phrases. Use hardware wallets for long‑term storage to keep keys offline, and separate hot and cold storage so most funds remain offline. Never store seed phrases digitally; write them on durable, tamper‑resistant material and consider a multisignature (multisig) setup if supported. Use unique, strong passwords managed with a reputable password manager, and practice careful seed phrase handling to prevent disclosure or scams.
How can I strengthen phishing protection and two-factor authentication to secure my crypto accounts on exchanges and wallets?
Phishing protection and strong authentication are critical. Enable two-factor authentication on all critical accounts, and prefer authenticator apps (like Google Authenticator or Authy) over SMS. Where supported, use hardware security keys (FIDO U2F/WebAuthn) for robust phishing resistance, especially on exchanges. Do not reuse 2FA tokens across services and store backup codes securely. For exchanges, enable withdrawal whitelists, require multi‑step confirmations for large moves, and regularly review connected devices and sessions. Bookmark trusted domains and educate household members about phishing signs to maintain secure exchanges and wallet access.
| Topic | Key Points |
|---|---|
| Crypto wallet safety and key management Intro note: Wallet safety is the cornerstone of cryptocurrency security. Your private keys are the keys to your kingdom; whoever controls them controls your funds. |
|
| Two-factor authentication (2FA) and strong authentication hygiene Two-factor authentication adds a critical layer of defense against credential theft. |
|
| Hardware wallets and cold storage as core defenses Hardware wallets are a cornerstone of cryptocurrency security best practices for long-term holders. |
|
| Phishing protection and user education Phishing remains a leading attack vector. Staying vigilant is a daily habit. |
|
| Secure exchanges and account hygiene A trusted exchange is a critical part of your crypto security posture. |
|
| Backup, recovery, and disaster planning Redundancy and recovery planning are indispensable. |
|
| Device and software hygiene Your devices are the gateways to your crypto assets. Maintain strong hygiene. |
|
| Advanced security measures and governance For communities or larger holdings, additional measures can elevate security further. |
|
| What to do if you suspect a compromise Despite best efforts, breaches can occur. Acting quickly minimizes damage. |
|
Summary
Cryptocurrency security best practices are essential for anyone holding digital assets, forming the cornerstone of a layered defense strategy. They emphasize combining strong wallet hygiene, robust authentication, hardware-based storage, awareness of phishing, and prudent exchange management into daily routines. A resilient security posture grows from ongoing education, routine checks, and capitalizing on safeguards like 2FA, multisignature, backups, and secure device practices. By embracing these principles, individuals can meaningfully reduce risk and preserve the integrity of their crypto investments in a dynamic threat landscape.